Quick Links
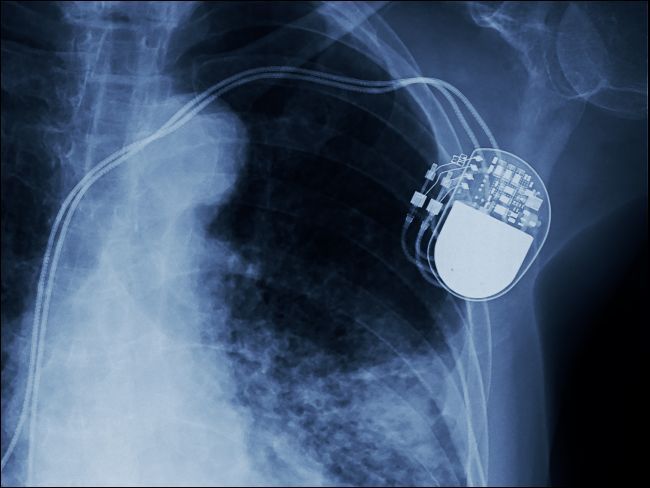
From pacemakers to smartwatches, we're increasingly becoming a cybernetic species. That's why recent headlines about vulnerabilities in implanted medical devices might set off alarm bells. Can your grandfather’s pacemaker really be hacked and, if so, what’s the real-world risk?
It’s a timely question. Yes, there are significant changes in medical technology afoot---implantable devices can now communicate wirelessly, and the coming medical Internet of Things (IoT) is bringing with it various wearable devices to keep healthcare providers and patients more connected. But a major medical device manufacturer has made headlines with not one, but two critical security vulnerabilities.
Vulnerabilities Highlight Hacking Risks
This past March, the Department of Homeland Security warned that hackers could wirelessly access implanted pacemakers made by Medtronic. Then, just three months later, Medtronic voluntarily recalled some of its insulin pumps for similar reasons.
On the surface, this is terrifying, but it might not be quite as bad as it sounds. Hackers can't access implanted pacemakers from some remote terminal hundreds of miles away or conduct broad-scale attacks. To hack one of these pacemakers, the attack has to be conducted in close physical proximity to the victim (within Bluetooth range), and only when the device connects to the Internet to send and receive data.
While unlikely, the risk is real. Medtronic designed the device’s communication protocol so that it doesn’t require any authentication, nor is the data encrypted. So, anyone sufficiently motivated could change the data in the implant, potentially modifying its behavior in a dangerous or even fatal way.
Like the pacemakers, the recalled insulin pumps are wirelessly enabled to connect to related equipment, like a metering device, that determines how much insulin gets pumped. This family of insulin pumps also don't have built-in security, so the company is replacing them with a more cyber-aware model.
The Industry Is Playing Catch-Up
At first glance, it might appear Medtronic is the poster child for clueless and dangerous security (the company didn't respond to our request for comment on this story), but it’s far from alone.
"The state of cybersecurity in medical devices is poor, overall," said Ted Shorter, Chief Technology Officer at IoT security firm Keyfactor.
Alaap Shah, a lawyer who specializes in privacy, cybersecurity, and regulation in health care at Epstein Becker Green, explains: "Manufacturers have not historically developed products with security in mind."
After all, in the past, to tamper with a pacemaker, you had to perform surgery. The entire industry is trying to catch up to technology and understand the security implications. A rapidly evolving ecosystem---like the medical IoT mentioned earlier---is putting new security stresses on an industry that’s never had to think about that before.
"We’re hitting an inflection point in the growth of connectivity and security concerns," said McAfee’s head threat researcher, Steve Povolny.
Although the medical industry has vulnerabilities, though, there’s never been a medical device hacked in the wild.
"I don’t know of any exploited vulnerabilities," Shorter said.
Why not?
"Criminals just don’t have the motivation to hack a pacemaker," Povolny explained. "There’s a greater ROI going after medical servers, where they can hold patient records hostage with ransomware. That’s why they go after that space---low complexity, high rate of return.”
Indeed, why invest in complex, highly technical medical device tampering, when hospital IT departments have traditionally been so poorly protected and pay out so well? In 2017 alone, 16 hospitals were crippled by ransomware attacks. And disabling a server doesn’t carry a murder charge if you’re caught. Hacking a functioning, implanted medical device, though, is a very different matter.
Assassinations and Medical Device Hacking
Even so, former Vice President Dick Cheney didn’t take any chances in 2012. When doctors replaced his older pacemaker with a new, wireless model, they disabled the wireless features to prevent any hacking. Inspired in part by a plot from the TV show, "Homeland," Cheney’s doctor said, "It seemed to me to be a bad idea for the vice president of the United States to have a device that maybe somebody might be able to...hack into."
Cheney’s saga suggests a scary future in which individuals are targeted remotely via medical devices regulating their health. But Povolny doesn't think we're about to live in a sci-fi world in which terrorists zap people remotely by tampering with implants.
"Rarely do we see interest in attacking individuals," Povolny said, citing the daunting complexity of the hack.
But that doesn’t mean it can’t happen. It’s probably just a matter of time until someone becomes the victim of a real-world, Mission Impossible-style hack. Alpine Security developed a list of five classes of devices that are most vulnerable. Topping the list is the venerable pacemaker, which made the cut without the recent Medtronic recall, instead citing the 2017 recall of 465,000 implanted pacemakers by manufacturer Abbott. The company had to update the firmware of these devices to patch security holes that could easily result in the death of the patient.
Other devices Alpine is worried about include implantable cardioverter defibrillators (which are similar to pacemakers), drug infusion pumps, and even MRI systems, which are neither bleeding-edge nor implantable. The message here is that the medical IT industry has a lot of work on their plate to secure all manner of devices, including large legacy hardware that’s sitting exposed in hospitals.
How Safe Are We?
Thankfully, analysts and experts seem to agree that the cybersecurity posture of the medical device manufacturer community has been improving steadily for the last few years. This is, in part, due to the guidelines the FDA published in 2014, along with interagency task forces that span multiple sectors of the Federal government.
Povolny, for example, is encouraged that the FDA is working with manufacturers to streamline testing timelines for device updates. "There’s a need to balance testing devices enough that we don’t hurt anyone, but not take so long that we give attackers very long runway to research and implement attacks on known vulnerabilities."
According to Anura Fernando, UL's Chief Innovation Architect of Medical Systems Interoperability & Security, improving the security of medical devices is a priority right now in government. "The FDA is preparing new and improved guidance. The Healthcare Sector Coordinating Council recently put out the Joint Security Plan. Standards Development Organizations are evolving standards and creating new ones where needed. DHS is continuing to expand upon their CERT programs and other critical infrastructure protection plans, and the healthcare community is expanding and engaging with others to continuously improve upon the cybersecurity posture to keep pace with the changing threat landscape."
Perhaps it’s reassuring that so many acronyms are involved, but there’s a long way to go.
"While some hospitals have a very mature cybersecurity posture, there are still many who are struggling to understand how to deal with even basic cybersecurity hygiene," lamented Fernando.
So, is there anything you, your grandfather, or any patient with a wearable or implanted medical device can do? The answer is a little disheartening.
"Unfortunately, the onus is on the manufacturers and the medical community," Povolny said. "We need more secure devices and proper implementation of security protocols."
There’s one exception, though. If you’re using a consumer-grade device---like a smartwatch, for example---Povolny recommends you practice good security hygiene. “Change the default password, apply security updates, and make sure it’s not connected to the internet all the time if it doesn’t have to be."